I would like to connect to a Postgres database on Amazon RDS. In addition to the typical Postgres connection details (host, port, user, password, database) that also requires SSH tunneling information (ssh host, port, user, password and private key). This information can currently not be provided in Exploratory when creating a connection. Is this something that could be added?
Yes! We’ll see what we can do here. Will update shortly!
Hi Peter,
Yes, Exploratory can connect to RDS through ssh tunnel to EC2 instance that is in the same Virtual Private Cloud as the RDS.
But if you are simply trying to connect to RDS, configuring your RDS’s Security Group, which does not require ssh tunnel setting, might be easier. Here is how.
-
On your RDS Dashboard, select your instance and click magnifier icon. It should look like the following.
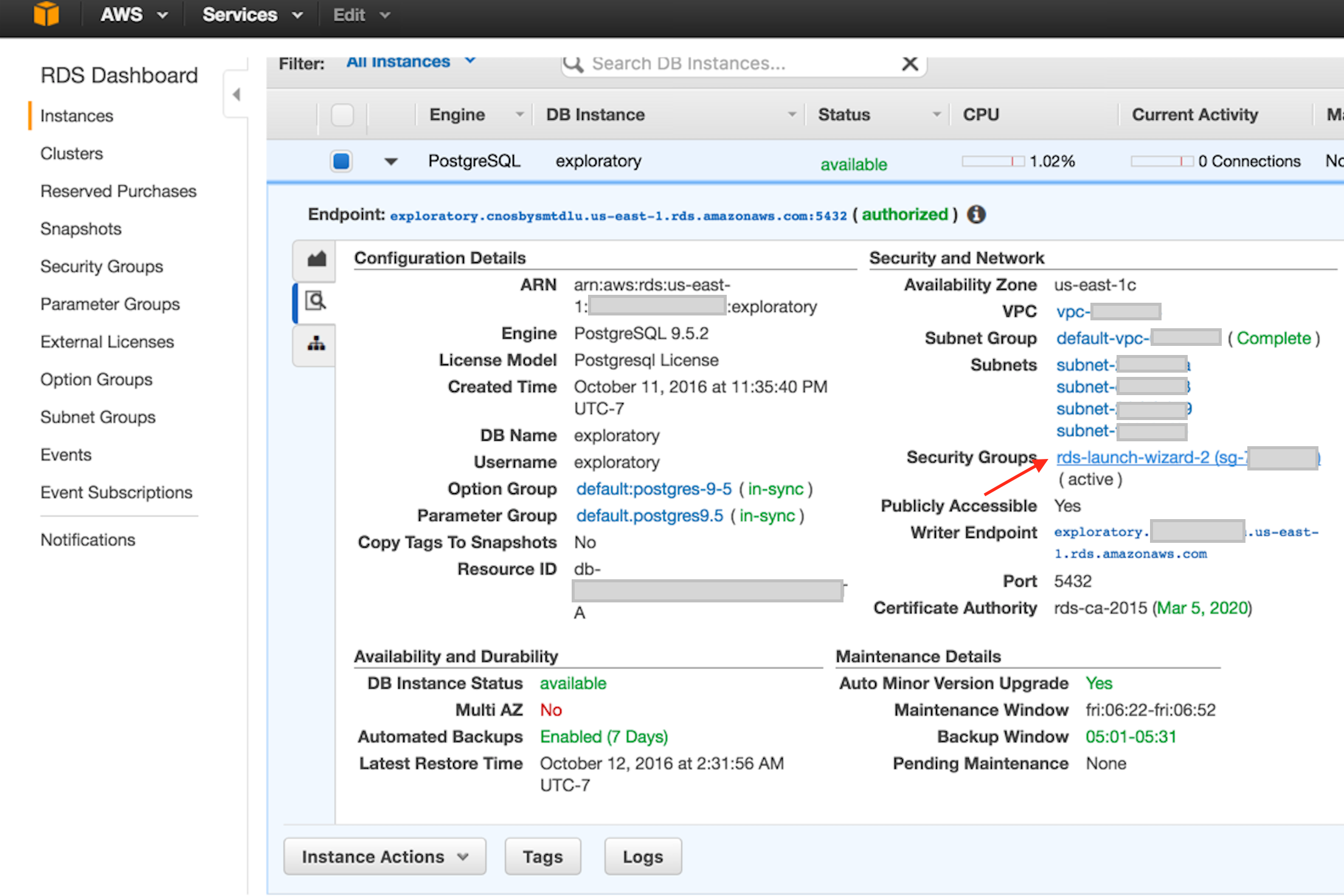
-
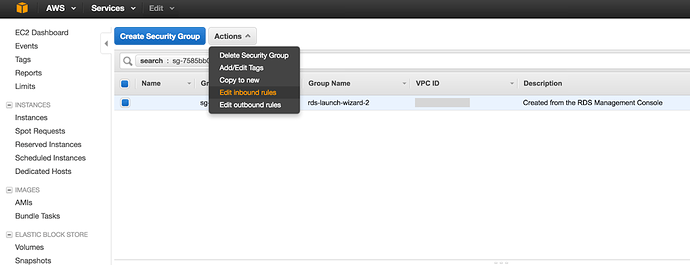
Click the Security Groups link on the above screen shot. Then you should see the Security Group config screen like the following screenshot.
-
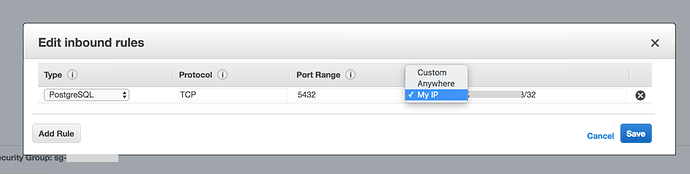
Click Edit inbound rules link on Actions dropdown box like the above screenshot. You should see a dialog box like following.
-
Click My IP like above screenshot. This will automatically detect your IP address and allow access from there. Then click Save.
-
Then you should be able to connect to this RDS instance by specifying host, port, database name, username, and password in Exploratory’s PostgreSQL data source dialog box.
Let me know if this works.
Or if you do need the ssh tunnel solution, let me know.
-Hideaki
Hi Hideaki, thank you for the thorough explanation. I checked with our AWS specialist and although what you suggest is indeed possible, it can only serve as a very temporary solution:
- Our IP-addresses might be dynamic
- Our users can work from home, so we would need to add IP addresses for each of them
- Our
publicly accessibleis set toFalse
So for us, it is not scaleable to maintain security like this and a SSH tunnelling option would be greatly appreciated. 
Hi Peter, OK, here is how to connect to RDS through a ssh tunnel.
- Set up an EC2 instance in the same Virtual Private Cloud as your RDS.
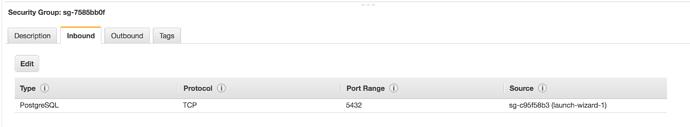
You need to have ssh access to this EC2 instance from the machine you run Exploratory. - Configure your RDS’s Security Group, so that it allows your EC2’s security group to connect for PostgreSQL.
Here is my config of RDS’s security group. The security group name in “Source” is my EC2’s security group.
- Set up ssl tunnel on your local machine
The following example would open your ssh tunnel, which listens at port 15432 of your local machine, and bridges the connection to the port to your RDS’s port 5432, through your EC2.
ssh -N -L 15432:your_rds.rds.amazonaws.com:5432 you@your_ec2.amazonaws.com
- Connect Exploratory
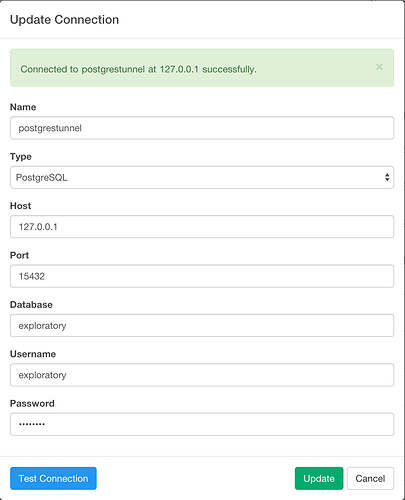
Connect your Exploratory to your local machine’s ssh tunnel port.
With above example, it would be 15432. Here is the screenshot of my Exploratory Connection config.
Let me know this works for you.
Thanks! That works.
Depending on how many other Exploratory users are using RDS, it might still be a good option to include this in the DB connection GUI.